DISK DRIVE ERASING/WIPING SOFTWARE
Green Pepper PRO
Technical Features
Technical Features
For details, check tutorials, manuals , and try download and free evaluation use!
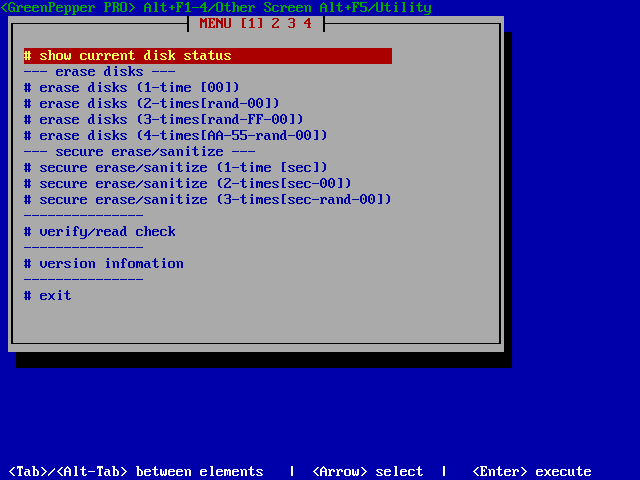
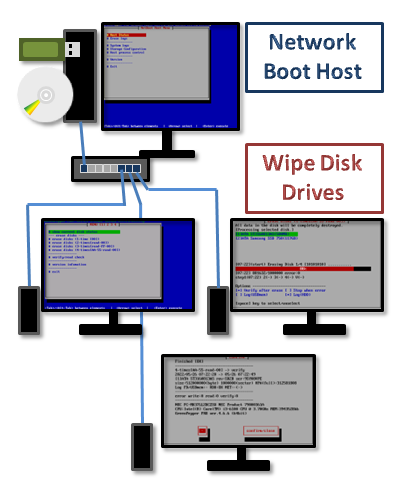
Erasure program boot from CD/USB flash drive/Network Boot.
One way to erase a disk drive is to boot from a CD/USB flash/network and run the program to erase it. Linux based system allows stable and fast erasure including Sanitize/Secure Erase.
Erasure program on Windows/WinPE
Another way to erase a disk drive is to use Windows based Erasure Application. Booting on WinPE, you can erase (including Sanitize/Secure Erase) Windows supported drives.
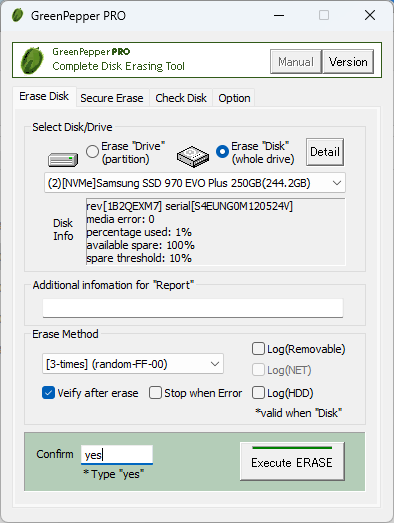
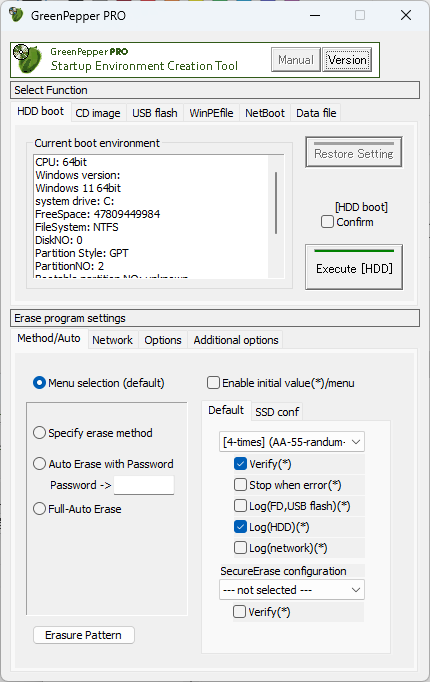
Customize your Erasure method.
This screen is used for creating bootable CD images and configuring USB flash drives.
You can specify various settings such as the erasure method and automatic erasure, and so on.
By distributing the created CD images or USB flash drives within your company, you can perform standardized erasure procedures with simple, error-free operations.
Supported Devices
Our software supports the vast majority of Windows PCs with Intel architecture. From tablets to laptops, desktops and servers.
The disk drives installed in these PCs will be erased.
The types of drives that will be erased include eMMC, UFS (>=ver4.8), ATA (IDE, SATA), NVMe, SCSI, SAS, FC, and USB drives.
Supported Erasure method
Over Write Erasure
1-Time erase (00)
2-Times erase (Random-00)
3-Times erase (Random-FF-00)
4-Times erase (AA-55-Random-00)
Secure Erase, Sanitize.
Write values are changeable.
*NIST SP 800-88, AR380-19, NSA(should change value), DoD5220.22-M compliant.
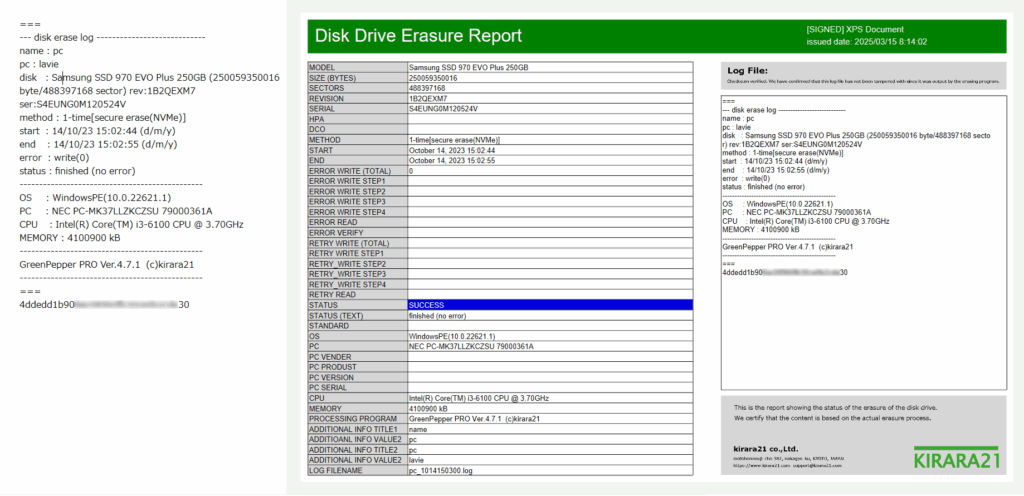
Log file and signed XPS Erasure Report
When managing data erasure within a company, keeping records of erasure is extremely important.
After the erasure, an erasure log file is created that contains information about the device and the details of the erasure. The log can be saved to a USB flash drive, the erased disk drive itself, or a network drive.
A checksum is added to the log file, making it possible to check for tampering.
Additionally, it is possible to generate a signed erasure report from the log file.
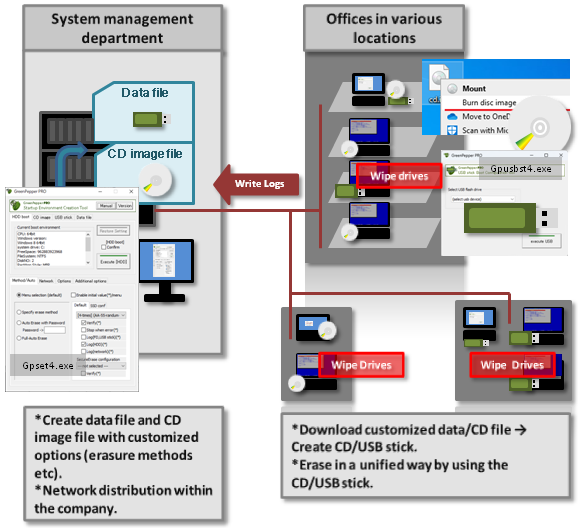
Implementing a unified security policy in the enterprise
The following usage scenarios are envisioned:
The system management department prepares an erasure program image based on the security policy formulated within the company. Each department obtains the erasure program from the company network and erases the PCs, and the erasure log is centrally managed by the system department via the company network.
Concentrated work using network boot
For commercial use or when working intensively with massive PCs in a company, the host function for Netowork Boot and the Network Boot function both provided by this software will greatly improve work efficiency.